In the Mailroom, Efficiency and Accuracy are Your Top Priorities.
Between sky-high document piles and data bottlenecks, how can you efficiently manage your mailroom scanners to accelerate information delivery?
The way you process information capture at the mailroom level has far-reaching effects. It impacts the core business operations at every level. When documents aren’t in the right place or when information is entered incorrectly, your business suffers.
Where is all your time currently going? To pre- and post-scan handling. To manual entry. To fixing errors. Legacy systems aren’t intelligent and rely heavily on operators to perform anything but the simplest tasks. Why put up with that? Now you can advance your mailroom with smarter scanning.
An intelligent capture solution will deliver lightning speed capture, classification, extraction, validation and delivery. Bring order to information chaos with intelligent scanning and sorting, at lightning-fast speeds – only from ibml.
Challenges
Slow Processes
Manual data entry, pre and post document scan sorting software, and QA processes are all time-intensive and slow down workflows.
Frequent Errors
Between manual data entry and scanning exceptions, errors are frequent – and are often uncaught before entry into downstream systems.
Data Jam
Clunky operational processes hold up your mailroom, creating a bottleneck of information that has far-reaching effects.
Varying Processes
You’re managing data from more sources than ever before – and antiquated systems need different processes for each document type.
The ibml Solution
Upgrade your mailroom with ibml intelligent capture solutions. Automate document capture, classification, extraction, validation, and delivery of information from any business input to accelerate mission-critical information delivery throughout your organization.

Accelerated Information Capture
Speed mailroom cycle times to get information to all decision makers quickly with the fastest mailroom scanners in the market. With co-mingled document scanning, in-line data capture, and document out-sorting, paper digitization has never been faster.
Shrink Your Operating Costs
Reduce your mailroom overhead by consolidating platforms, labor, maintenance and the real estate required to process documents. Minimize operator training, enhance productivity and scalability of your operations.
Upgrade Your Security and Compliance
Secure sensitive information from the moment it enters your organization with role-based access to functions and information, complete document audit trails, activity logging, and data encryption.

Reduce Downstream Exceptions
Ensure accurate and usable information is delivered to downstream systems. Reduce exceptions and catch errors early with automated validation, superior image quality, and image processing tools.
ibml-as-a-service (iaaS)
Harness the Latest Technology
Without the Upfront Costs
Gain an unbeatable technological advantage while freeing up your cash flows. With the new ibml-as-a-service, you can utilize ibml’s cutting-edge capture technology on a pay-as-you-go basis by opting for fixed quarterly payments. With greater flexibility and freedom, you’ll be able to avoid high CAPEX costs, preserve cash for other core growth initiatives, and customize, scale and bundle your technology subscription to fit individual needs. Plus, your investment is 100% tax deductible and eligible for upgrades or new features at any time.
Gain an unbeatable technological advantage while freeing up your cash flows. With the new ibml-as-a-service, you can utilize ibml’s cutting-edge capture technology on a pay-as-you-go basis by opting for fixed quarterly payments. With greater flexibility and freedom, you’ll be able to avoid high CAPEX costs, preserve cash for other core growth initiatives, and customize, scale and bundle your technology subscription to fit individual needs. Plus, your investment is 100% tax deductible and eligible for upgrades or new features at any time.
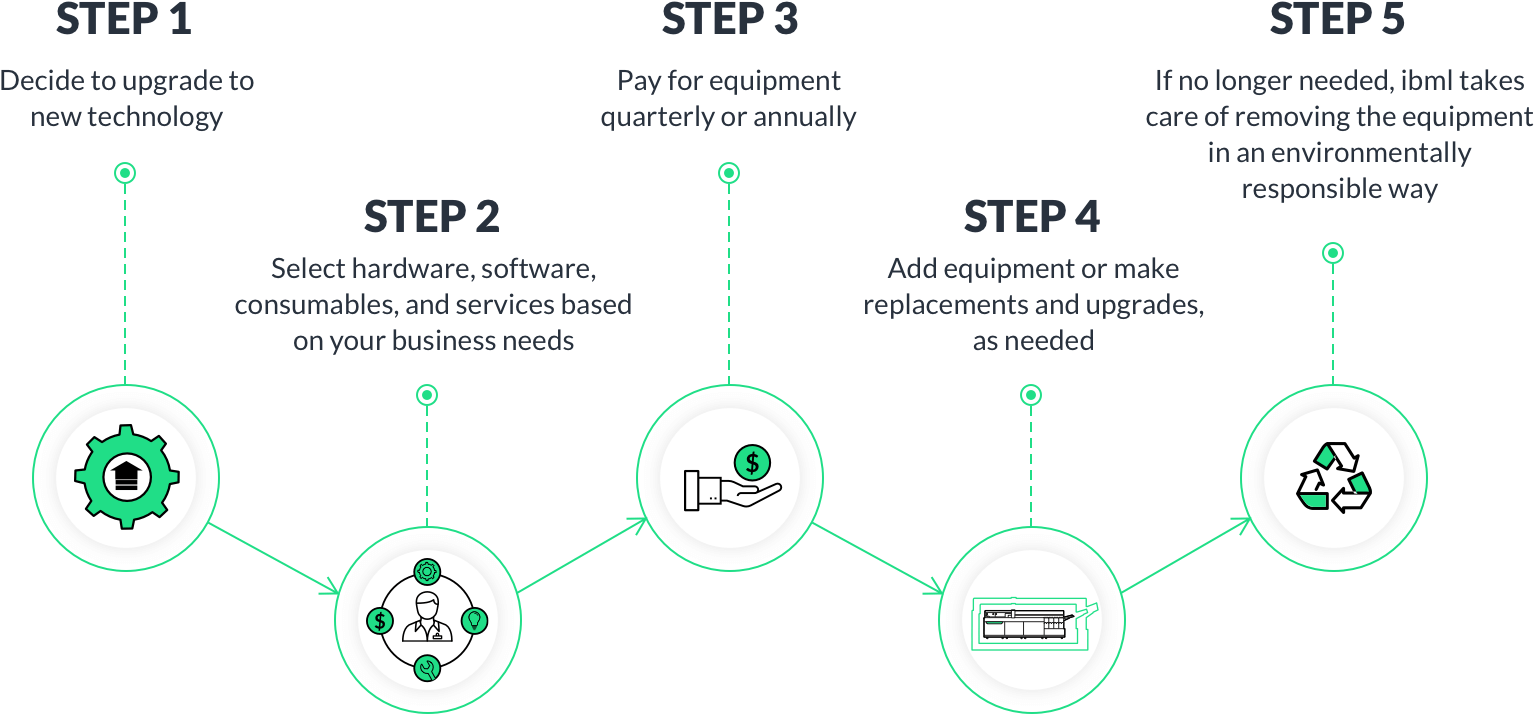
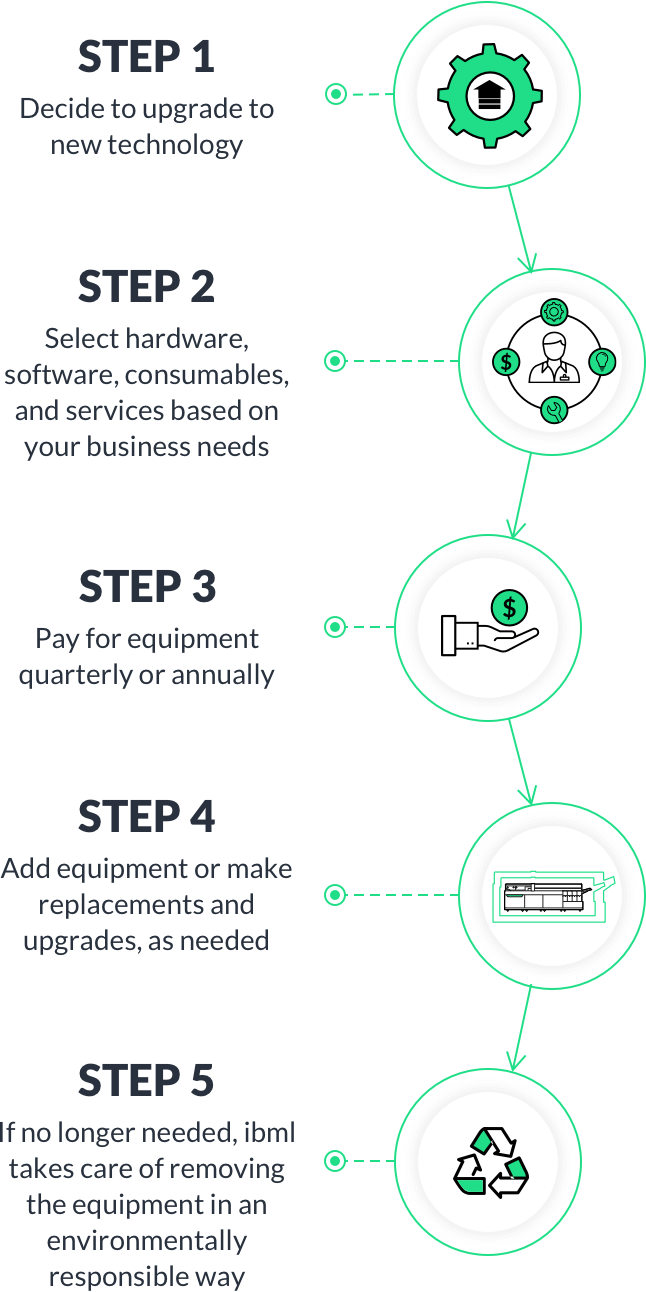
How the iaaS subscription process works: